General structure of a Styx message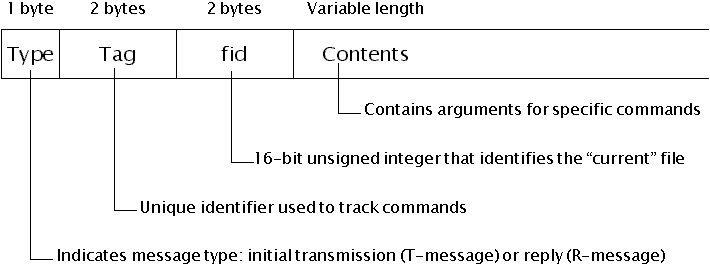
The second field, Tag, is a chosen by the client to identify the message. The client must ensure that no two outstanding messages on the same connection have the same tag. The reply tag will have a value one greater than the request that generated it except in the event of an error reply (Rerror).The fid field is a file identifier that is part of Styx messages that operate on files. Every file that is manipulated by the operating system is identified by a fid. The Contents field contains one or more parameters.
Each parameter consists of a fixed number of bytes (except the data fields of write requests or read replies). In the message descriptions below, the number of bytes in a field is given in brackets after the field name. The two-, four-, and eight-byte fields may hold unsigned integers represented in little-endian order (least significant byte first). Fields that contain names are 28-byte strings (including a terminal NUL (zero) byte).
Other than the NUL terminator, all characters are legal in file names. Systems may choose to reduce the set of legal characters to reduce syntactic problems, for example to remove slashes from name components, but the protocol has no such restriction.
Inferno names may contain any printable character (that is, any character outside hexadecimal 00-1F and 80-9F) except slash and blank. Messages are transported in byte form to allow machine independence.
Message Tag
Each T-message has a tag field, that chosen and used by the client to identify the message. The reply to the message will have the same tag. Clients must arrange that no two outstanding messages on the same connection have the same tag. An exception is the tag NOTAG, value 16rFFFF, meaning 'no tag'. The client can use the NOTAG message, when establishing a connection, to override tag matching in messages.A client can send multiple T-messages without waiting for the corresponding R-messages, as long as all outstanding T-messages have different tags. The server may delay the response to a request on one fid and respond to later requests on other fids. For example, this may be necessary when the client reads from a file that the server synthesizes from external events such as keyboard input.
![[Top]](Top.gif)
![[Prev]](Previous.gif)
![[Next]](Next.gif)